
Author: Abhiram Cherukupalli
Mentor: Dr. Alberto De La Torre Duran
Disha Delphi Public School
Abstract
Quantum cryptography is one of the most researched fields of Information Theory. New theoretical cryptographic protocols are constantly being developed and realized experimentally. Fundamentally these cryptographic protocols are rendered secure by the laws of quantum mechanics. In this review, we introduce the concepts of quantum mechanics, the idea of measurement collapse, the uncertainty principle and some insightful solutions of the Schrodinger Equation. Then, we discuss the EPR paradox, Bell’s Theorem leading up to Entanglement and Quantum Cryptography. Next, we examine the Standard Classifications of cryptographic Protocols, the no-cloning theorem, basic protocols like the BB-84 protocol and other similar protocols like bit commitment and entanglement based protocols. Finally, we review their experimental realizations and a few protocols beyond standard key distribution.
1. Quantum Mechanics Background:
A. The Wave Function:
In classical mechanics we can predict the position x(t) and momentum p(x,t) of a particle as a function of time (t) when given the initial conditions and the forces acting on the particle [1]. However, in quantum mechanics that is not the case. Rather we attempt to find the wave function Ψ(t) of the particle.
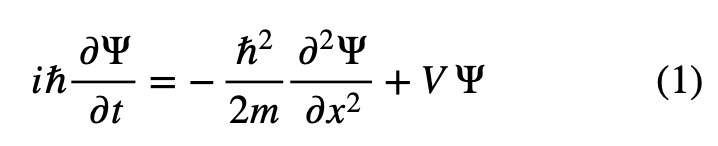
This seemingly arbitrary function has an important physical significance, given by Born’s statistical interpretation: 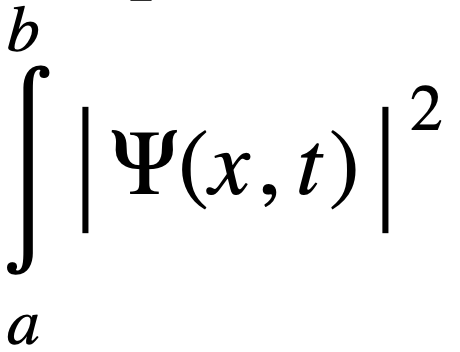 dx signifies the probability of finding a particle between a and b at a time t given its wave function.
dx signifies the probability of finding a particle between a and b at a time t given its wave function.
This means that quantum mechanics is indeterminate, that is, you cannot predict the outcome of any experiment, but you can gain statistical information about all the possible outcomes. However, we can say with certainty that the particle has to be somewhere in space and time. Therefore, we can normalize the wave function (provided it is square integrable).
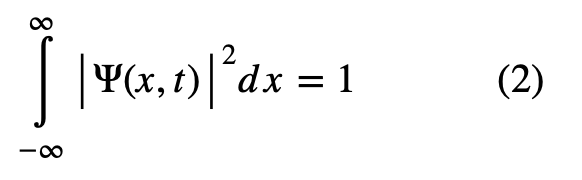
This is useful for determining the magnitude of the complex multiplicative factor A (note that we cannot determine the phase of A by normalization), as if Ψ(x,t) is a solution to (1), so is A • Ψ(x,t).
An important consequence of the Schrödinger equation is that if a wave function is normalized at any time, the normalization remains preserved [1]. If the normalization hadn’t been preserved, then all wave functions would become non-normalizable (not physical states) and the whole theory would collapse as the Born’s interpretation would be deemed incompatible with the Schrödinger’s equation.
B. What happens when you make a measurement:
Let us assume an arbitrary wave function of a particle (Figure 1), with probabilities of being at different points.
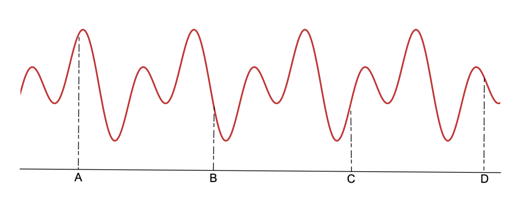
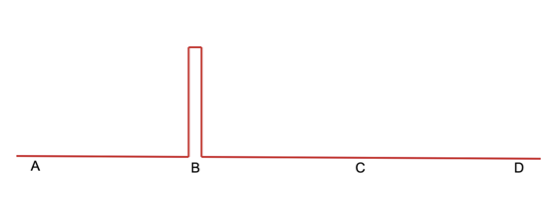
Figure 2: The collapse of the wave function into a delta function when the particle was found at B.
After the measurement, the wave function instantly spreads out, while obeying the Schrödinger equation but with different initial conditions, so the wave function gets modified.
Now, the question arises, when we measured the particle to be at B at some time t0 where is B just before the measurement?
There are three different positions scientists take on this question:
- The realist position: The realist believes that the particle was at C and quantum mechanics could not predict it, making it an ”incomplete theory” that needs a hidden variable along with the wave function for it to be rendered complete. They believed that nothing is indeterminate, and that indeterminacy is just a reflection of our ignorance.
- The orthodox position: The particle was not anywhere. You only know where the particle is when you make a measurement, otherwise, its position is indeterminate, and it can be anywhere. We compel the particle to attain a definite position by measuring it.
- The agnostic position: The agonist believes that the in-determinacy problem is indeterminable. Because you must make a measurement to know the state of a system, you cannot know the state of a system between measurements.
Interestingly Albert Einstein was a realist, as he believed quantum mechanics defied causality. All these positions were popular among scientists until the Bell’s theorem was postulated (Sec I.F). This “indeterminacy” of Quantum mechanics leads to a fundamental quantum mechanical principle.
C. Heisenberg Uncertainty Principle:
There is a famous example to explain the Uncertainty Principle: suppose you have a rope which is tied to a wall on one end and is held by you on the other end. The rope is the “medium” in which the wave travels in. Now if you periodically move the string up and down and generate a wave (Figure 3). We can find the wavelength of this wave, but if you ask me the position of the wave, it would not be defined as the wave is “everywhere” so there is no clearly defined position unlike the wavelength.
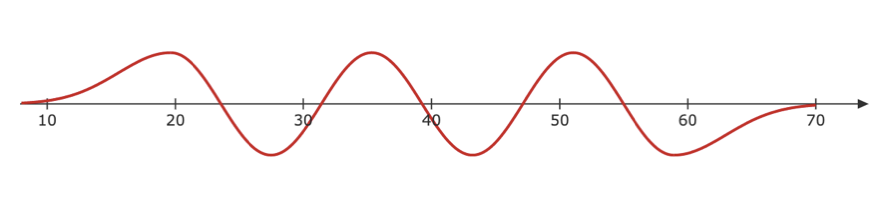
Now what if I produce a wave with a jerk, it is possible to find the position of the wave as the wave is not periodic, so we cannot determine its wavelength.
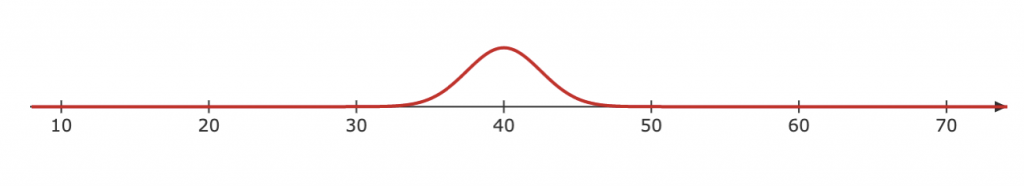
There seems to be a trade-off between the precision of wavelength and position: The more precise a wave’s position the less precise its wavelength and vice versa.
So, if the wavelength of the particle is less precise, its momentum is also less precise and its position is more precise. Mathematically the Heisenberg Principle is given by:
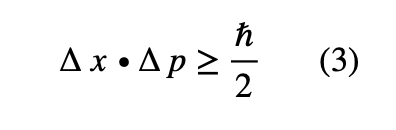
When we come to solve the Schrödinger’s Equation, for simplicity we try to find separable solutions for the wave function. Separable wave functions are simple products: Ψ(x,t) = Ψ(x) f(t) (4)
Such separable solutions are important, because as we will see soon when we combine separable solutions we can obtain a general solution. If we assume the wave function is separable then we can simplify the Schrödinger equation to obtain a time independent form:
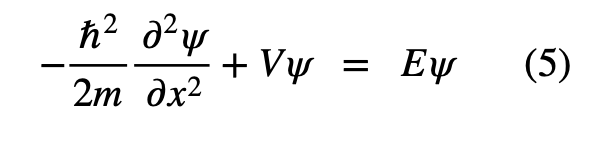
- They have a definite total energy: The Hamiltonian in classical mechanics is the sum of kinetic and potential energies of the system:
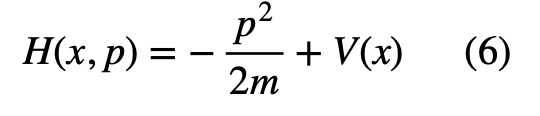
So, we can rewrite the Schrödinger equation as:
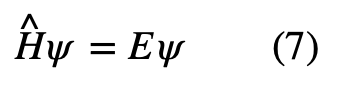
Where, E is the eigen-value of the Hamiltonian operator.
2. The general solution to the Schrödinger Equation (1) is a linear combination of separable solutions.
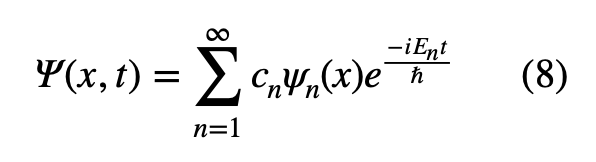
It happens to be that every general solution to the Schrödinger equation can be expressed as a linear combination of separable wave-functions, all we need to do is adjust the constant Cn [1].
3. It renders a stationary problem: Though the wave function in (8) has a time-dependent factor, the probability function doesn’t.
E. The EPR paradox:
Coming back to our discussion of what happens when we take a measurement, Einstein, Podolsky and Rosen believed in the realist interpretation. These three came up with the infamous EPR paradox.
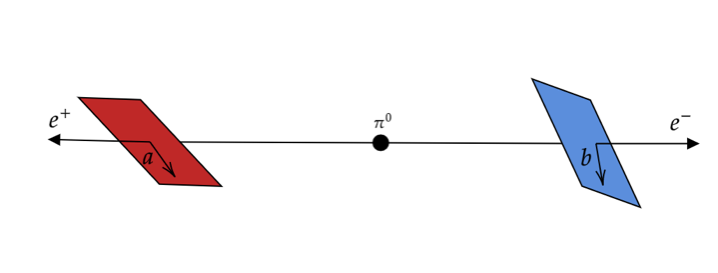
Assume we have a neutral pi meson (of zero spin) which decays to produces an electron-positron pair, π0 -> e+ + e–. Since spin angular momentum should be conserved, the spin of the electron and positron must be opposite in sign. Therefore, if the spin of the electron is measured as spin up ↑ the spin of the positron as spin down ↓ is automatically measured. Quantum mechanics cannot tell you what the spin would be deterministically. All it tells you that no matter how far apart they are their measured spins must be of opposite parity. This implies that as soon as one of the particle’s spin is measured, the wave function of the other particle collapses instantaneously. Einstein and other realists felt such “spooky action at a distance” to be impossible, because if the mutual wave function collapse was instantaneous, then the travel speed of the causal influence between them appears to be faster than light. A Paradox!
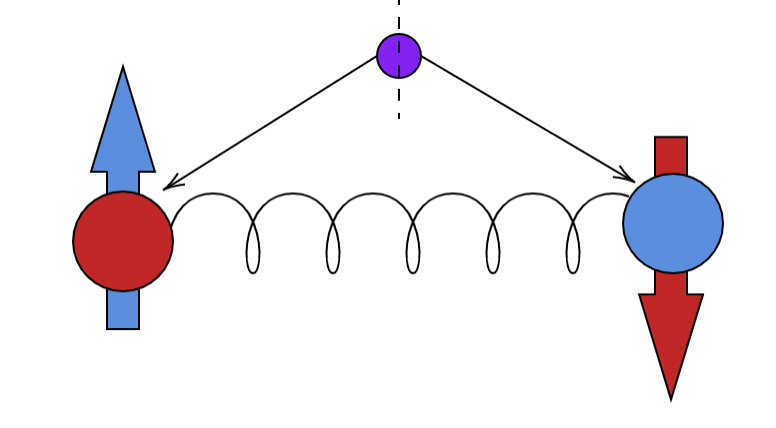
The realists believe that the electron always had spin up since the time it was made and, quantum mechanics being incomplete, was not able to predict the spin as it needed some hidden variable to be complete. They did not believe quantum mechanics to be wrong, they believed it was incomplete.
F. The Bell’s Theorem:
Different hidden variable theories were put forward in the following decades, but none were considered plausible. Considerable theoretical work was put into finding a hidden variable theory, but without success until J.S. Bell came along, who proved that any hidden variable theory is incompatible with quantum mechanics [2].
The idea is as follows: We orient the detectors in a non-parallel direction, allowing them to rotate freely. Let P(a, b) denote the average of the product of the spins measured by the detectors oriented along unit vectors a and b, as shown in Figure 6.
If ![]() then we get back the original EPR orientation such that
then we get back the original EPR orientation such that ![]() . Similarly,
. Similarly, ![]() . Quantum mechanics predicts that for any configuration
. Quantum mechanics predicts that for any configuration ![]() .
.
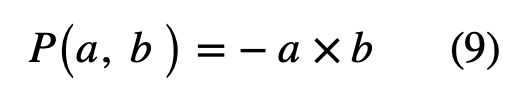
If there is a hidden variable needed to describe the complete state of both the particles, then some new functions ![]() give the results of the electron and positron measurement successfully (Here we assume that the electron measurement is independent of orientation of b). We can see that
give the results of the electron and positron measurement successfully (Here we assume that the electron measurement is independent of orientation of b). We can see that ![]() . Also:
. Also:
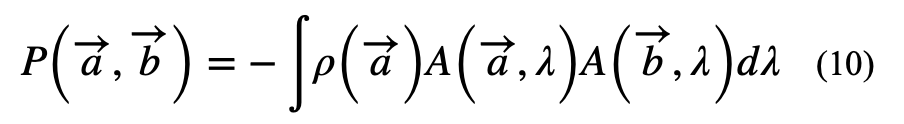
If ![]() is another unit vector on simplifying (10) we arrive at:
is another unit vector on simplifying (10) we arrive at:
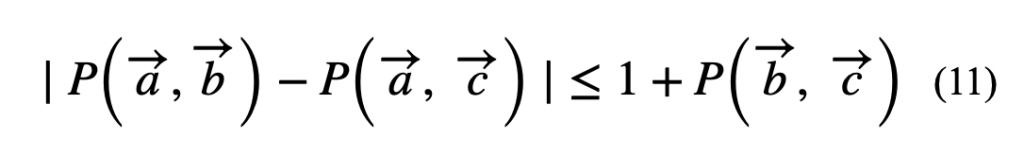
This can be proven to be inconsistent with quantum mechanics by taking all three vectors in the same plane with ![]() making angle 45° and 90° with
making angle 45° and 90° with ![]() respectively. Clearly the inequality in (11) will not hold, implying that there can be no hidden variable theory that can save us from the non-locality of quantum mechanics.
respectively. Clearly the inequality in (11) will not hold, implying that there can be no hidden variable theory that can save us from the non-locality of quantum mechanics.
The Bell’s inequality was tested in 1970 by Aspect, Grangier and Roger [3] and the results were in agreement with quantum mechanical prediction and was incompatible with the Bell’s inequality. This shocked the physics research world as this proves nature being fundamentally non-local.
But why is non-locality so disturbing? How can the influence between the electron and positron travel faster than light?
To explain this, we have to make an important distinction: A causal influence cannot travel faster than the speed of light, but other influences, such as instantaneous wave collapse, could. The latter influences carry no energy; hence, they are by no circumstance bound to be traveling slower than light. This is proven by the no-communication theorem, which states that during the measurement of one of the particles, it is not possible for one observer to communicate information to another observer, thereby preserving causality.
2. Quantum Entanglement:
States such as the EPR pair, where there is an inherent dependency of one particles measurement on the other, are called entangled states. Any composite state of two quantum systems A and B can be represented as: HA ⨂ HB where HA and HB are their respective Hilbert spaces having base states ![]() , and ⨂ represents the tensor product:
, and ⨂ represents the tensor product:
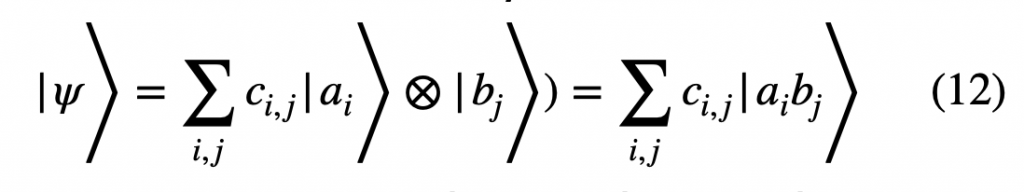
If ![]() can be written as
can be written as ![]() the state is said to be separable, otherwise it is entangled.
the state is said to be separable, otherwise it is entangled.
For example, the EPR configuration can be represented as:
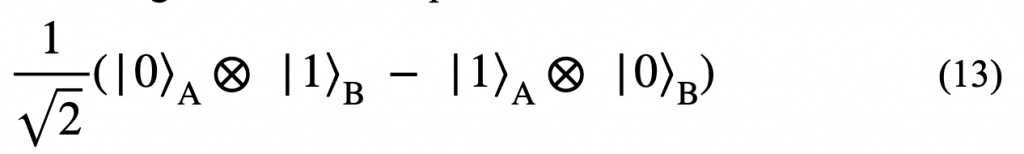
It is impossible to separate this wave function into ![]() , thus making this configuration entangled. If Observer A measures 0, the state of the system becomes
, thus making this configuration entangled. If Observer A measures 0, the state of the system becomes ![]() and vice versa.
and vice versa.
3. The idea of Quantum Cryptography:
“No measurement can be made without perturbing the system.”
This unusual property of quantum mechanics underlies the core concept involved in secure communication channels. If, for example, two people, Alice and Bob, want to communicate with each other quantum information (e.g., photons carrying the information). Eve, an eavesdropper, cannot obtain any information without perturbing the system, thus revealing her presence. Alice and Bob can simply check whether someone is eavesdropping by comparing the data that is passed through the public channel. This would be of no use, though, as they will get to know of eavesdropping after the data transfer takes place. However, when this idea is complemented with a key, it can ensure privacy before any data transfer. A key is a random sequence of bits (qubits), which is sent through the channel. If the key is unperturbed, it means the data channel is secure, so the parties can start sending information encoded in the keys [4, 5].
4. Cryptography:
Cryptography is the science of constructing protocols that prevent eavesdroppers from reading private encrypted messages. An algorithm can be used to achieve this, with the help of a key to encrypt the message. For it to be considered secure, it should be impossible to unlock a cryptosystem without its key. Modern cryptosystems can be broadly divided into two categories.
Asymmetrical cryptosystems: Also known as public-key cryptosystems, Alice and Bob use different keys. Bob prepares a public key using a secret private key and Alice uses this public key to encrypt a message which can be decrypted only by Bob’s private key. A classical version of this protocol is prime factorization. Given the prime factors of a large number, it is easy to compute the number but it becomes much harder in the other direction (Computing 127*71*7 is easy but given 63119 it is much harder to find the prime factors). That is, a type of a one way function. Fortunately, the backward process can be made easier if one of the factors is known, in this case the key. However, prime factorization isn’t “proven” to be secure.
Symmetrical cryptosystems: Both Alice and Bob use the same private key to encrypt and decrypt the message. Let us assume, Alice adds a key (k) to the message (m) in a binary system s = m ⨂ k now Bob can simply subtract k from Alice’s message and decrypt it. This system is provably secure because s is as random as m and hence it doesn’t contain any information so it is provably secure. However, notable disadvantages exist with this cryptosystem: Alice and Bob must possess the same private key (which must be longer than the message itself). This key must be pre-shared in a secure manner and also should necessarily be used only once (like a one-time password). This is because, if the same key is used twice Eve can gain some information about the messages by just adding the public messages (sA ⨂ sB = mA ⨂ k ⨂ mB ⨂ k = m1 ⨂ mB using commutation). Interestingly, asymmetrical cryptosystems are often used to send the private sessions key used in symmetrical cryptosystems.
If these cryptographic algorithms were broken by advances in mathematics, Quantum Cryptography would be the only solution.
5. Shannon Information Theory:
Information can be thought of in terms of randomness, that is, entropy or probability. If a certain event is likely to occur, you gain lesser information from it; higher the probability of occurrence lesser is the information transferred. This entropy is represented mathematically by using Shannon Entropy or Information entropy (H):
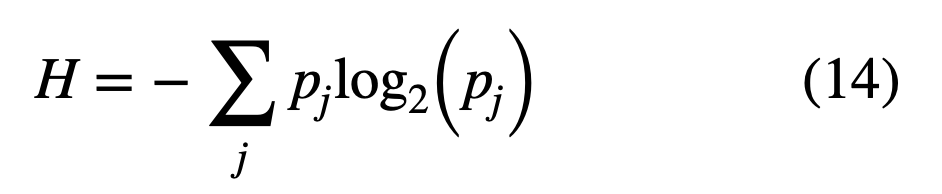
where pj is probability of occurrence of jth value. Shannon, continued this discussion, in 1984 by proving that no matter how noisy a channel is, it is possible to communicate data, almost error free, up to a maximum number known as the channel capacity which only depends on the statistics of the channel [6].
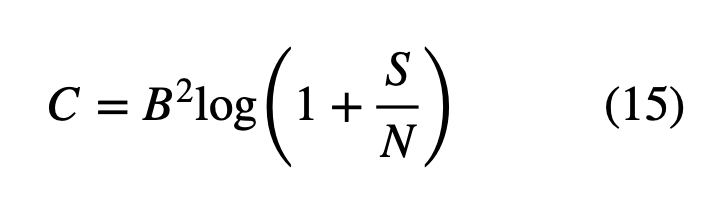
where C is the channel capacity (maximum bit rate), B is the bandwidth of the Channel, S/N is the signal-to-noise ratio where S is the average signal power received and N is the average power of the noise. Similarly, we can think of this quantum mechanically, where Eve gains information from a quantum tunnel between Alice and bob at the cost of introducing noise into the system which lowers the bit rate. It is a constant tug of war between perturbation and information.
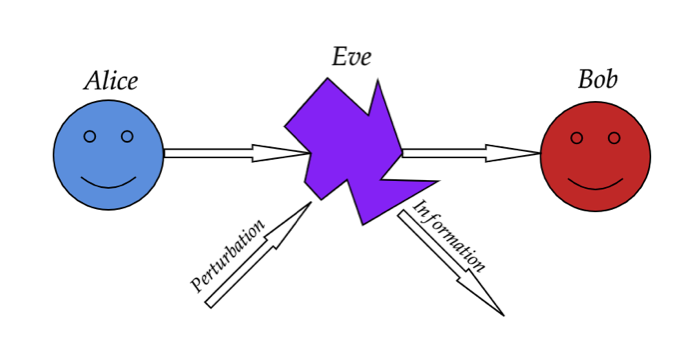
6. The No-Cloning theorem:
Suppose Eve intercepts the message between Alice and Bob, she could just measure the quantum state and then resend a duplicate of it without perturbing the system, staying “undetected”. Conveniently as a consequence of quantum mechanics it can be proven that “no arbitrary quantum state can be perfectly cloned”. This is the no-cloning theorem. An intuitive proof for this statement is that if we could make perfect copies, then the person could make as many identical copies as he wanted and measure every parameter with arbitrary precision, thereby breaking the uncertainty principle.
However, remember that the no-cloning theorem only prevents against making perfect copies, but you can make as many “imperfect” copies as you want. It is important to note than non-orthogonal states can never be perfectly cloned so whatever Eve does should bring in some errors.
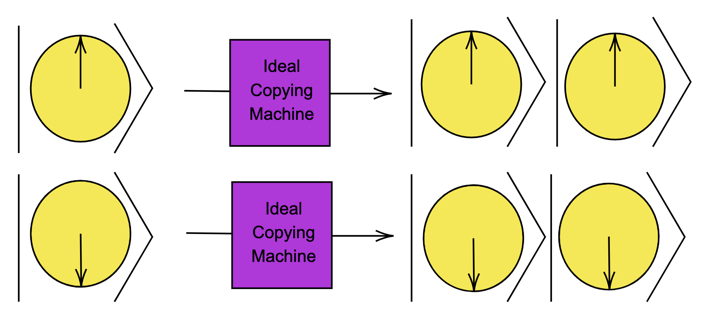
Figure 10: Depiction of an ideal copying machine which clones the states |0> and |1> perfectly
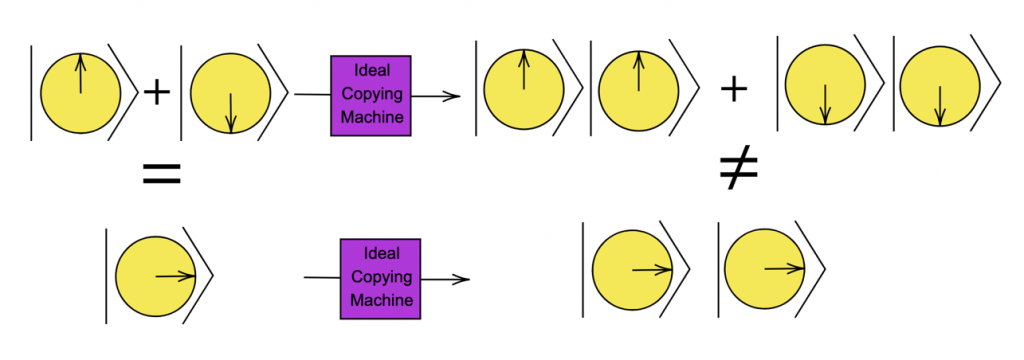
Figure 11: If such an ideal cloning machine did exist then it would give the wrong answer for the superposition state of |0> + |1> [7].
7. The BB-84 protocol:
This protocol, aptly called the BB84 protocol, was proposed by Charles H. Bennett and Gilles Brassard in 1984 at the IEEE conference in India [8]. In this protocol Alice encodes the bit in a polarization state of a photon in one of two non-orthogonal bases either rectilinear or diagonal. The binary 0 state is defined as 0° polarization in the rectilinear state or a 45° polarization in the diagonal state. Similarly, a Binary 1 state is defined as 90° polarization in the rectilinear state or a 135° polarization in the diagonal state.
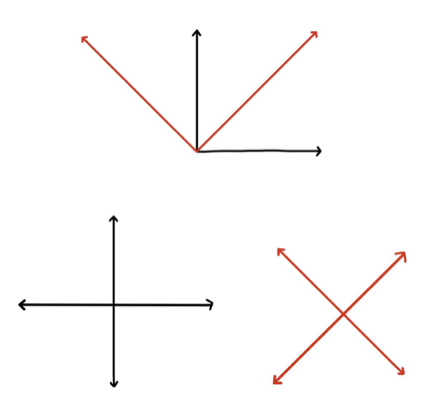
Figure 12: Polarized states in the BB84 Protocol
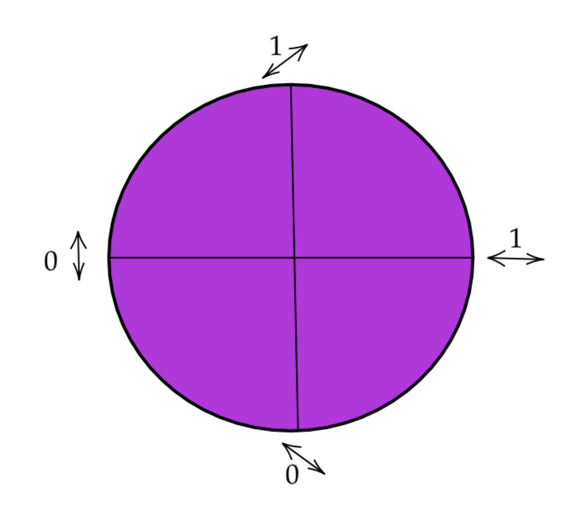
Figure 13:The Bases of BB 84 protocol
Initially, Alice sends a key to Bob over a quantum channel. First, she chooses a random string of bits (for the binary states) and a basis for each bit to get a polarized state. Alice then sends her qubits to Bob, who measures the photons using a random non-orthogonal basis. If Bob chooses the same basis as Alice then he would get the same polarization (if no one eavesdropped on the photon). If, however, Bob chooses a different basis the qubits he reads would be random. Next, Bob discloses the bases he chose to Alice over a public channel (but, importantly, he does not disclose his result). Alice reports which bases are correlated and they discard the other bits where the bases are not correlated. If Eve does not eavesdrop on the channel both Alice and Bob would have the same perfectly correlated key called the sifted key. However, the crucial step, is that both Alice and Bob agree upon a random subset of the bits, and they compare them. If there is no measurement error or noise in the channel, the bits will be perfectly correlated and if they are no, it reveals the presence of Eve, who modified the photon by measuring it. If there was a measurement error, then error correction protocol can be used (Sec X.). Due to the Quantum No-cloning Theorem, Eve cannot replicate the photon she measures as she doesn’t know with certainty the quantum state of the photon.
However, how safe really is this protocol? To answer, let us assume Eve intercepts the photon (an imperfect copy) and re-sends it to Bob (the intercept-resend strategy). Eve has to guess the random base and she has a 50% chance of guessing it right. A total of 25% of Bob’s bases will be uncorrelated which gives Eve a maximum of 75% probability of not being detected. If the string of bits is long enough this probability will tend to 0 (as it depends on (3/4)n [9].
8. The One time pad:
Classically, a One-time pad can be achieved if Alice and Bob have an arbitrarily long pre-shared secret key which is used to encrypt and decrypt the messages. In theory, Alice could measure her classical system with arbitrarily high precision and then use the one-time pad to securely communicate this information to Bob, who can then, in principle, reconstruct (a copy of) the classical system. This however will not work in a Quantum Cryptographic Algorithm.
Let us say Alice wants to send a copy of a quantum system to Bob, she cannot do that as that violate the no-cloning theorem. However, they could share a quantum key and a classical channel. Alice could “teleport” her quantum state to Bob without gaining any information about the quantum state, while Bob would end up with a state isomorphic with the original state (but he doesn’t learn anything about the quantum state). This was aptly called “quantum teleportation” [10].
This is the only provably secure QC, you can show that if the quantum channel used to the share the key was secure, so is the one time pad [11, 12].
9. Other Similar Protocols:
A. Quantum Bit commitment and Coin-tossing:
A.1 Bit commitment:
Continuing with our two communicating parties, let us suppose that Alice chooses a bit (0 or 1), which she commits to, and wants to show Bob the evidence that she, indeed, has a bit in mind and cannot alter it. However, with this evidence, Bob should not be able to figure out the bit Alice chose. In case Alice changes her bit after commitment, it is considered as cheating, which a bit commitment protocol should protect against.
As it surprising turns out, there can never exist any bit-commitment protocol which is secure! This can be proved rigorously [13], but I would like to focus more on the implications of the impossibility of a bit-commitment protocol, it means that we could never trust Alice! She could cheat all she wants without Bob finding out.
A.2 Coin Flipping:
Similar to the idea of bit-commitment is that of coin flipping. Assume Alice and Bob are far away from each other and playing a game. The idea of the game is that one of Alice and Bob, say Alice, flips a coin, and the other, Bob, guesses the face of the coin. If the guess is correct, then Bob wins. Otherwise, Alice wins. However, in a classical coin tossing game, we could never know if Alice cheated. Of course, with the use of a trusted third party who flips the coin this problem is solved, but what if we could make a protocol that solely relied on the laws of quantum mechanics to ensure no cheating in this coin-flipping game without the help of any third party. If a secure bit-commitment protocol was available, then making this coin-flipping scheme would be trivial (But, importantly not the other way around). It just so happens that as long as Alice and Bob do not share any entangled state, any quantum flipping scheme would be impossible. Another really fascinating outcome of quantum mechanics! It shows that Alice can really cheat if she wanted without Bob finding anything out [14].
For a while it was believed that these classical protocols have “provably unbreakable” quantum counterparts, but quantum bit commitment and ideal coin tossing was also proven to not be secure [15].
B. Entanglement-Based Protocols using the Bell’s theorem:
B.1 Eckert E91 protocol:
Continuing with our two communicating parties, let us suppose that Alice chooses a bit (0 or 1), which she commits to, and wants to show Bob the evidence that she, indeed, has a bit in mind and cannot alter it. However, with this evidence, Bob should not be able to figure out the bit Alice chose. In case Alice changes her bit after commitment, it is considered as cheating, which a bit commitment protocol should protect against. As it surprising turns out, there can never exist any bit-commitment protocol which is secure! This can be proved rigorously \cite{Chiribella_2013}, but I would like to focus more on the implications of the impossibility of a bit-commitment protocol, it means that we could never trust Alice!
She could cheat all she wants without Bob finding out. In this protocol a quantum channel sends two entangled particles (preferably polarized photons) one each for Alice and Bob. They choose on a random basis and they correct their raw keys, as in the BB84 protocol to obtain the sifted keys. If there was no eavesdropping, Bob’s key would be the perfect complement of Alice’s key. Here is the interesting part: to know whether Eve was peeking into the quantum channel, all they need to do is measure the photons where they used two different bases, now they measure the photons in a third predetermined base and then compare their results. If their results obeyed the Bell’s inequality (which does not hold for entangled particles), it reveals the presence of Eve as the photons are no longer entangled [16].
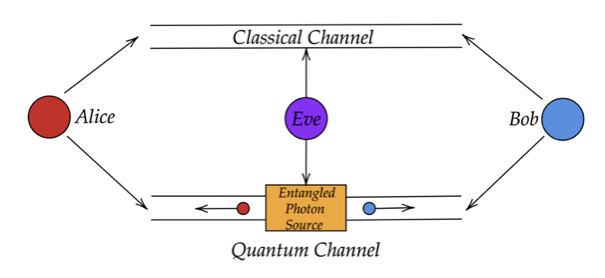
Figure 14: The Eckert entanglement protocol
B.2BBM92 Protocol and Other Variants:
Bennet and Brassard in 1992 made a variation of the E91 protocol which does not require the Bell’s test. Similar to the E91 protocol there is an entangled photon source, Alice and Bob make measurements on a random basis, and they publicly announced their bases. Therefore, when they are correlated the spin must be opposite. If it isn’t, it reveals the presence of Eve. Furthermore, Bennet and Brassard proved that any variant of the BB84 protocol could be adapted to use an entangled photon source without the use of the Bell test [17]. Enzer, in 2002, proposed another entanglement-based protocol, which is an entangled version of the Six-State Protocol [18].
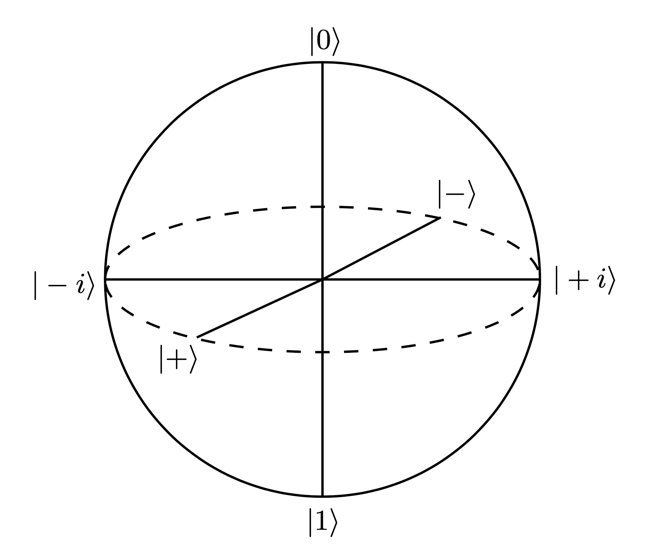
Figure 15: The Six-State Protocol
10.Eavesdroppers, their strategies and How to Counter Them:
If their bases are correlated, Alice and Bob should, in theory, have identical sifted keys. However, in reality that is not the case as there are many errors that are introduced, which eavesdroppers capitalize on. To counter them we need to apply some information protocols:
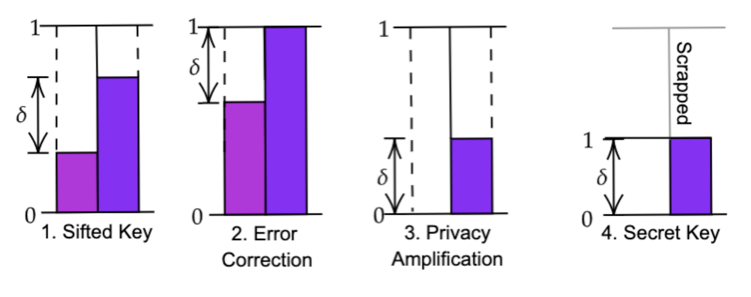
1. Error Correction: The error rate, called the quantum bit error rate, QBER (to avoid confusion with the classical Bit error rate BER) is usually of the order of a few percent. This error rate would be reduced down to the order of using classical algorithms.
2. Privacy Amplification: After error correction, both Alice and Bob have the same sifted keys. However, Eve might still have information; this is where privacy amplification comes in. It reduces the information Eve has to almost zero. We assume that Alice, Bob and Eve respectively have the variables α, β, ε and their entire probability distribution is P(α, β, ε). Both Alice and Bob know what P(α, β) is, and from (16) we obtain a lower bound on S(α, β || ε), the conditions for a non-negative secret key rate.
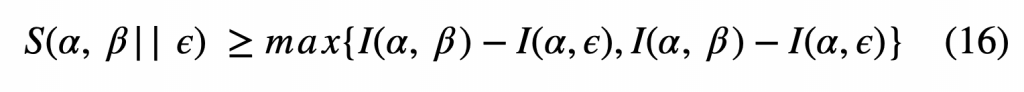
To establish a secret key using this idea, Alice and Bob compare a random subset of their sifted keys and estimate the QBER. If (16) is not satisfied ,they stop the protocol, and if it is satisfied they continue on with error correction protocols. In other words, as Alice and Bob share an identical key, they can transform their key into a new shortened key in such a way that Eve cannot gain information unless she also has an identical key. Therefore, even if Eve has substantial information on the key, it would be of no use after privacy amplification.
The aim of eavesdropping analysis is to find “ultimate proofs” (security that works against all types of eavesdropping attacks) for cryptosystems. Eavesdropping attacks that Eve carries out are broadly classified into two categories:
- Individual attacks: Here, Eve attaches independent probes to each photon individually, and measures each probe, one at a time. It is also known as an Incoherent Attack.
- Joint attacks: In the most general case of a joint attack, Eve can measure multiple probes at once coherently; hence, they are also called coherent attacks. A commonly used subset of a joint attack is the collective attack, which assumes that each photon is probed only once but many probes can be measured at once.
Individual attacks can be translated into a classical problem using the idea of privacy amplification of imposing constraints on the joint probability distribution using the laws of quantum mechanics.
A.The Intercept resend strategy:
Assuming we use the BB84 protocol, we know that there is a 25% QBER and Eve gains 0.5 bits of information for each qubit measured. From Shannon Information theory, we know that the amount of information Eve gains is the amount of entropy decrease.
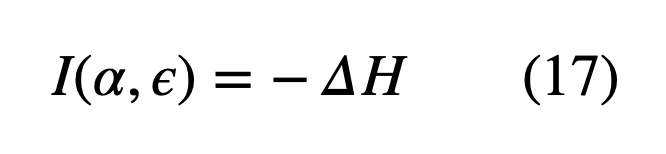
where I(α, ε) denotes how much information Eve ε has on Alice and H is the Shannon entropy. We can simplify (17) using (14) and the fact that Hinitial is 1 as Alice’s bit is uniform. We find, as expected, that Eve gains 1/2 a bit for each qubit measured.
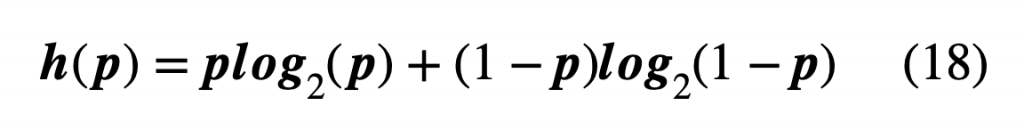
In addition, the probability of Eve guessing the correct bit is 0.75 (as expected). However, if Eve measures the bit in an intermediate basis, the Breidbart Basis.
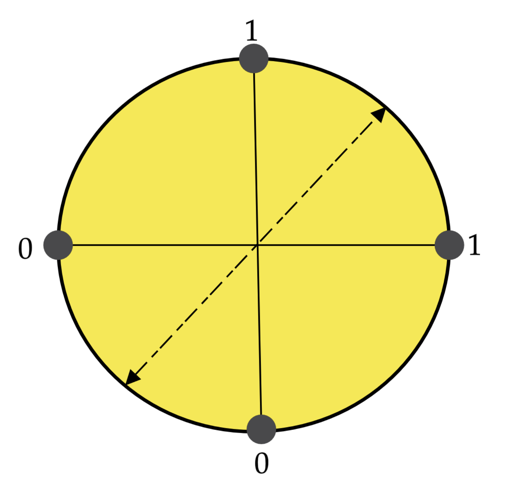
Figure 16: The Briedbart basis
Then the probability that she gets the bit correct is cos2(π/8) =0.85 and curiously by using (18) we find that Eve only gains 0.4 bits per qubit but has a higher probability of getting it right, this is because in the Breidbart basis in half of the cases the information is deterministic, but in the regular BB84 protocol the information is always probabilistic.
B.“Ultimate” security proofs for any noisy channel:
In an ideal channel with no noise, it is easy to prove that quantum cryptography (QC) is secure. However, it is interesting to note that this proof can be extended to any noisy channel provided the equipment is perfect. Obviously, QC is only secure up to a threshold of QBER which is what we need to find. The proof provided in [4] uses two theorems:
α, β, ε
Theorem 1: For a given joint distribution P(α, β, ε), Alice and Bob can form a shared secret key if and only if I(α, β)≥ I(α, ε) or I(α, β) ≥ I(β, ε). In other words, this means that Bob must have more knowledge of Alice’s bits than Eve does. This can be understood visually in the figure below.
Theorem 2: If Eve performs a measurement giving her some information I(α, ε) then, because of the perturbation, there is a limit on the amount of information Bob can gain. If n is the number of qubits, which Bob receives, that are in the same basis then Theorem 2 implies that:
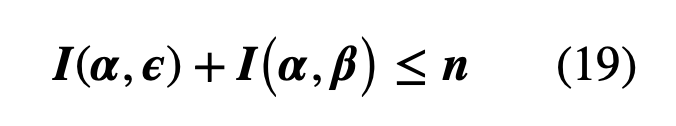
Essentially, information per qubit both Bob and Eve gained when combined should be ≤ 1. Combined with (18), we obtain:
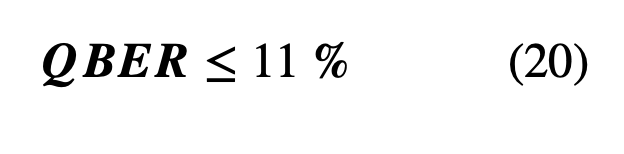
Therefore, whenever (11) is obeyed, an ultimate security protocol can be developed. Note that this proof is valid only when the key is much longer than the number of qubits Eve intercepts.
11.Two way quantum communication protocols:
Two-way quantum protocols have a distinct advantage over unidirectional protocols in that they are deterministic. Generally, in a two-way protocol, Bob prepares quantum states and sends them to Alice via the quantum channel, who encodes the states and re-sends it back to Bob, who performs a measurement. There are two common two-way protocols: The LM-05 protocol and the ping pong protocol.
A. LM-05 protocol:
Here Bob sends of qubit in one the forms | 0 >, | 1 >, | + >, | – > . Alice does one of two things to this qubit, she either uses this qubit as a control to test with a probability of c (control mode) or uses it to encode information (encoding mode), with a probability of 1-c. The way Alice tests for noise is similar to the BB84 protocol, wherein she measures the qubit on a random basis. In the original protocol, Alice now sends the qubit back with the exact same wavelength, amplitude, time gap, or else Eve could determine Alice’s chosen mode.
However, this is not feasible in real life. Instead, Alice encodes this bit into information and re-sends it to Bob, who decodes it using the same base he sent the qubit in. As we can observe, this is a deterministic protocol as Bob know Alice’s bases without a need for base-reconciliation which would be non-deterministic. In addition, for the two-way tunnel protocol to work, a direct test on at least one direction of the tunnel is necessary. Therefore, a two-way quantum tunnel protocol is susceptible to attacks such as the Trojan horse attack (Sec 12.C). without the control mode [19, 20].
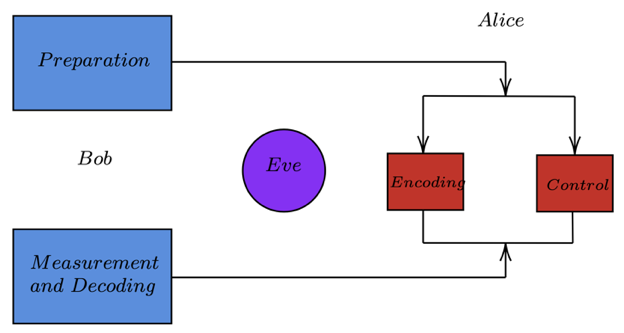
Figure 18: The LM-05 Protocol: Bob Prepares a Qubit and sends it to Alice who uses the qubit as a control or to encode information. She sends the encoded bit to Bob who decodes it.
B. Ping Pong Protocol:
In the ping-pong protocol, an entangled orthogonal state is used in the following form:
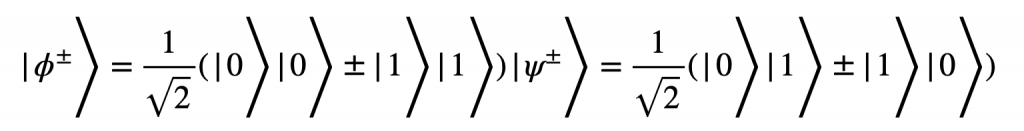
As you can see they are just the EPR states. What Bob does is that he makes two, qubits one being the home qubit and the other being the travel qubit. Bob sends this travel qubit |Ψ+> to Alice who randomly chooses whether to do a message mode or control mode. Let us assume that Alice chooses the message mode and encodes the qubit she received from Bob using an encoding operation ![]() where b is either 0 or 1. If b = 0 then the qubit |Ψ+> will be transformed into |Ψ–>. However, if b=1 it will be left untouched. Alice sends this encoded bit to Bob who performs a Bell measurement to get the wave function to be one of |Ψ+> , |Ψ–> hence revealing the value of b [21].
where b is either 0 or 1. If b = 0 then the qubit |Ψ+> will be transformed into |Ψ–>. However, if b=1 it will be left untouched. Alice sends this encoded bit to Bob who performs a Bell measurement to get the wave function to be one of |Ψ+> , |Ψ–> hence revealing the value of b [21].
If instead Alice chooses the control mode, she measures the qubit in basis {|0>,|1> } and then reveals the result publicly to Bob, now Bob also makes a measurement in the basis {|0>,|1> } and announces his result. If their results do not differ it indicates the presence of Eve and the protocol is aborted.
12.Real life examples:
A. Photon Number Splitting (PNS) Attacks:
The entanglement protocols are difficult to work with in real life, as modern-day equipment cannot reliably produce and measure singular photons. In real life, a laser produces a number of coherent photons. Eve can exploit this by splitting off a small number of photons for each qubit and lets the rest of the photons pass on to Bob, leaving no trace. This attack is called the photon number splitting or PNS attack [22].
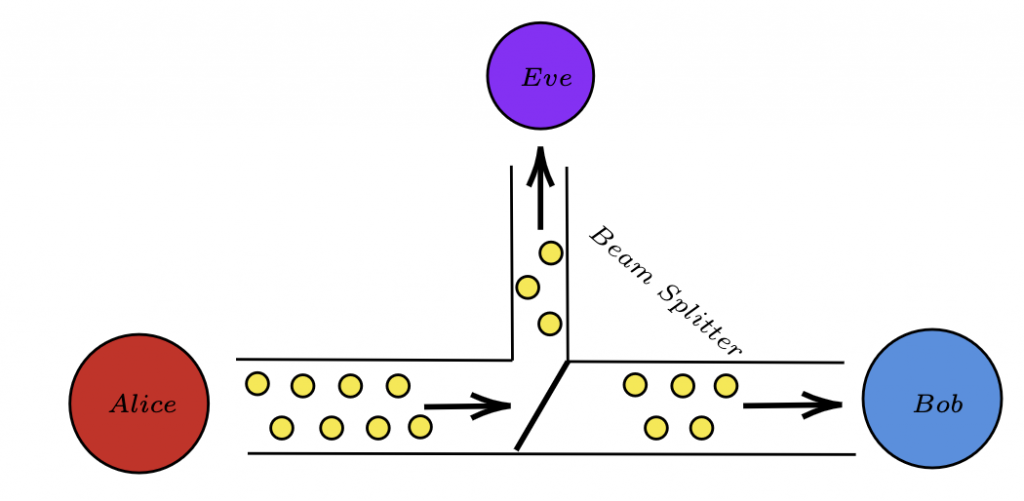
This attack can be countered in two ways: the first is the SARG-04 protocol where Alice does not reveal her bases publicly but reveals a pair of non-orthogonal states in which the bit might be encoded in. If Bob measures on the same basis, he would have measured one of the non-orthogonal states and, if not, they simply discard the bit. Now, all Eve can do is guess, so her Shannon information is significantly lower [23]. Unfortunately, the SARG-04 protocol, which was theorized to be the same as the BB-84 protocol, but experimentally it under performs due to errors introduced [24].
The second method uses decoy pulses where Alice sends the beams of varying intensities, with only one being the signal pulse and all others being decoy pulses. The so called “Decoy State Protocol”. With the help of these decoy pulses Alice can detect the presence of Eve as she cannot maintain the bit error rate when multi-photon sources are involved [23, 25, 26].
Accounting for more such real-life quantum channel imperfections, Gottesmann’s paper [27] explains the real life security of BB84-based protocols.
B. Intensity Based Attacks
When Huang tested the decoy state protocol in real life using a source that could regulate the intensity, he found that different intensities in general corresponded to different times at which the pulses were sent [28] This means theoretically, Eve can differentiate between a decoy pulse and the actual signal according to the time of sending. However, Alice can counter this attack by modulating the intensity of the photons after they are sent, and it was found that when an external modulator was used, all photons were simultaneous. However, as recently discovered Eve can heat up Alice’s source using high-intensity sources, and this shifts the timings of different intensity pulses, Alice cannot compensate for this time delay unless she finds out that they have been changed [29].
C. Trojan Horse Attacks:
Trojan horse attacks are a classic case of QC, which reminds us that the security of QC is not determined just by the laws of Quantum mechanics but it also depends on the technical measures. In this attack, Eve sends a light pulse through a quantum channel, in this case an optical fiber, entering Alice’s or Bob’s detector, and then Eve analyzes the reflected light. This provides her information about the polarization settings of the apparatus by calculating the phase shift. We cannot however, simply just block the optical fiber as it would not allow for communication between Alice and Bob. To be protected against this attack, Alice should first reduce the time period, ∆ tphase , in which a phase shift occurs to the order of nanoseconds, forcing Eve to send the pulse at the same time as Bob.
Next, Alice using an attenuator reduces the energy of the pulse from Bob to, let’s say 0.2 photon per pulse. For, Eve to gain, say 1 photon per pulse she has to send a photon of twice the energy. Alice, can easily detect the sudden increase in energy in Bob’s pulse which reveals Eve. However, Eve could however send ultra-short pulses (a low ∆tphase or could use a pulse of different wavelengths. So, Alice must use an optical band-pass filter which allows Alice’s transmission to go through with a bandwidth compatible with the ∆ tphase . Trojan Horse Attacks, though preventable using technical measures, are threatening attacks and should be kept in mind while making a channel [30-33].
In principle, a back-flash attack is similar to a Trojan horse attack, an avalanche photodiode (APD) in real practice emits some light when it measures [34]. This “back-reflected” has a lot of information in it, for example, its polarization could give information about the basis Bob used and even gives information about Eve’s source.
D. Faked State Attacks:
As we found from the PNS attack, the light is not really a single photon but a bunch of photons. Thus, detectors can echo the effect of a single photon using very weak light sources. This reliance on weak light sources is exploited in the faked state attack. The core weakness is the APD of Bob, which is supposed to measure only one photon by registering a click, but an APD has a certain recharge time (in the order of µs ). This implies that if a beam of light is shone on the diode continuously then the diode cannot recharge and hence it just becomes a classical photodiode. Further, this also implies that Eve can adjust the timing of the light to essentially control the time at which the detector clicks and forces Bob to unknowingly use Eve’s basis. It is called a faked state attack because Eve does not actually send a quantum state, but rather makes Bob’s detector think it is detecting a quantum state [35-38].
This can be illustrated by an example in which Eve detects a bit 1 of base X from Alice, she sends a photon of opposite bit (bit 0) and opposite basis W to Bob and while sending this “faked” state, she simultaneously shines continuous light onto Bob’s 1 bit detectors, blinding them. If Bob measures the bit in basis X, he has a 50% chance of not detecting anything, and if he measures anything other than in base X.
13.Protocols Beyond Standard Key Distribution:
A. Quantum random access codes (QRAC):
The principle of random access codes is simple, Alice needs to encode n bits into m and send them to Bob (n > m), and Bob should be able to recover all the bits with probability > p. Such a random access code is represented by ![]() .
.
Classically, you encode n-classical bits into m classical bits, but you could however encode them into m-qubits. Here is where it becomes interesting, when Bob recovers one bit, the whole wave function collapses, risking the loss of other bits. Therefore, there will always be a threshold probability for Bob to recover all the bits [39]. Let us investigate this!
A.1 Visualizing qubits using Bloch Spheres:
A qubit is a composition of bits |0⟩ and |1⟩. So, it can be represented as: |ψ⟩ = A|0⟩ + B∥1⟩ and since ψ must be normalized, A2 +B2 = 1. Therefore, we can write (without the loss of generality)
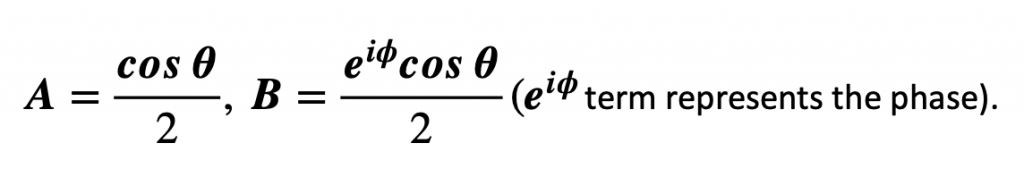
This can be re-interpreted in a spherical coordinate system:
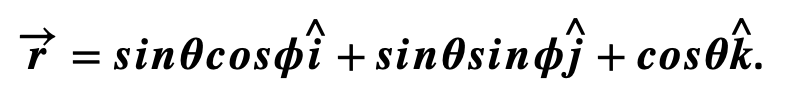
This is the Bloch Sphere.
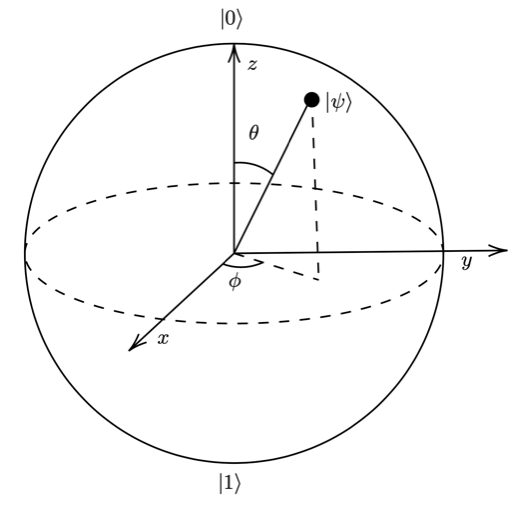
Figure 20: The Bloch Sphere
From this representation we can find the probability of |ψ⟩ collapsing to |φ0⟩ to be 1/2(1 + cos θ) [40]. For a QRAC, the probability threshold is just ![]() QRAC, the probability threshold is just
QRAC, the probability threshold is just 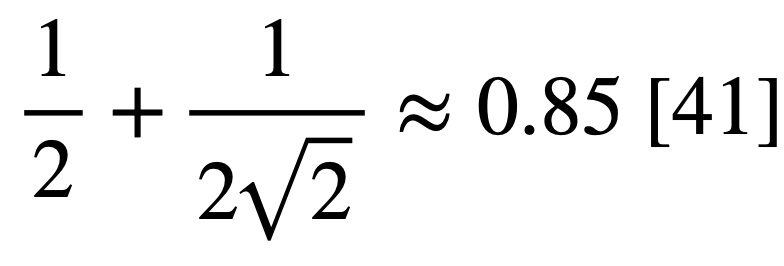 , and for
, and for ![]()
![]() . Let us assume the minimum probability threshold is 0.5 (better than a coin flip). For a
. Let us assume the minimum probability threshold is 0.5 (better than a coin flip). For a ![]() to have a probability greater than 0.5, a sphere must be divided into 2n parts by n planes. As you can see, in the figure below, it is possible to cut a sphere into four parts using two planes and eight parts using three planes, but it is impossible to cut a sphere into 16 parts using four planes, we can at most cut it into 14 parts. Hence a
to have a probability greater than 0.5, a sphere must be divided into 2n parts by n planes. As you can see, in the figure below, it is possible to cut a sphere into four parts using two planes and eight parts using three planes, but it is impossible to cut a sphere into 16 parts using four planes, we can at most cut it into 14 parts. Hence a ![]() never works for p>1/2 [43].
never works for p>1/2 [43].
A.2 Communication complexities:
The main aim of finding communication complexity is to calculate the number of communication bits that Alice and Bob must exchange in order to perform a certain task. The simplest example is that proposed by Yao [44], where Alice and Bob each have bits x and y, bits, respectively. They need to send these bits to a third party (the referee), and then all three collectively need to calculate the value of a function f(x, y) while minimizing the amount of information used.
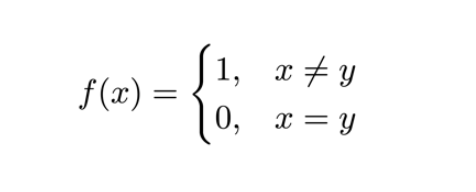
A trivial communication strategy is just Alice sending x to the referee and Bob sending y to the referee but this is highly inefficient with a complexity of $O(2n)$ (sending two bits of length n). The “communication cost” of this strategy could be highly reduced if only a part of the bit is sent instead of the whole bit. This is where tools like Quantum fingerprinting can be applied, and used to distinguish two strings by using the least number of bits. Instead of comparing the entire string, only the fingerprint of the string will be compared which reduces the communication complexity significantly.
Another way to decrease the communication complexity is to use the concept of shared randomness, where since Alice and Bob are entangled, less amount of information transfer is needed.
B.Quantum Data Locking (QDL):
The idea behind QDL is pretty simple, Alice and Bob initially share no mutual information, now Alice using a key of length k encodes a n-bit message into a n-bit code-word sends the code-word to Bob. They now share a mutual information of n. When Alice shares the key, the mutual information could potentially increase by more than k by quantum mechanical means. Now, the regular BB84 protocol follows but with an important difference: in QDL Eve is assumed to be able to store quantum information only for a limited time or a limited amount of information can be stored at any time. What this means is that, if Eve intercepts n qubits she has to measure them instantaneously (or after some time), she cannot gain all the information. The amount of information that Eve can extract from a quantum system is called the accessible information; in this case Eve can only have a maximum information of n/2.
Thus, Eve loses half the information, and if the length of the bit is long enough the information Eve has would be negligible. In addition, for any QDL protocol to be deemed “good”, the length of the message transferable should be much greater than the length of the key itself. QDL works best for locking information in quantum states using exponentially small pre-shared keys [45].
C. Quantum Digital Signatures (QDS):
In cryptography, many a times we need to verify the origin of a message. This can be achieved by using a digital signature.
A classical digital signature is very similar to the way asymmetric cryptosystems work, by using one-way functions (Given x we find f(x) but not the other way around). A common one-way function used is prime-factoring, but as we know, no provably secure one-way function has been found. For example, the prime factoring function is not secure against a quantum computer. This leaves a hole in cryptography which quantum signatures attempts to fill.
A QDS Scheme ensures that:
1. The message was created by the sender, which he cannot deny
2. The message has not been tampered with
3. The message if accepted at one receiver should be acceptable at all receivers
C.1 The Gottesman Chaung Protocol:
The Gottesman-Chaung protocol uses the ideas of quantum one-way function, similar to classical one way functions, they return a public quantum bit-key from a private classical/quantum string [46]
In a simplified Gottesman scheme, we consider the former case of using a classical string. It goes as follows:
Alice has to sign every bit in the message. For this she chooses R pairs of private keys ![]() , where all
, where all ![]() will be used to sign bit 0 and all
will be used to sign bit 0 and all ![]() will be used to sign bit 1. The function
will be used to sign bit 1. The function ![]() is public and Alice converts
is public and Alice converts ![]() and
and ![]() into
into ![]() and
and ![]() , the public quantum keys. She can make as many identical copies of these keys as she wants but more the number of copies lesser the security of the system. ,Now she sends this to Bob, who now has the bit a, private keys, and their corresponding public keys. Bob now uses the ka calculates the value of
, the public quantum keys. She can make as many identical copies of these keys as she wants but more the number of copies lesser the security of the system. ,Now she sends this to Bob, who now has the bit a, private keys, and their corresponding public keys. Bob now uses the ka calculates the value of ![]() .
.
However, a problem arises here, let’s say we have two quantum states ![]() and
and ![]() . how do we find out if they are the same? Classically this problem is trivial, as we can just look at the strings and find out if they are the same. However, it becomes interesting when we look at it quantum mechanically. We perform the SWAP test to achieve this, instead of delving into the details, all we need to know about the SWAP test is that it is non-deterministic. There is always a probability that it gives you the wrong answer.
. how do we find out if they are the same? Classically this problem is trivial, as we can just look at the strings and find out if they are the same. However, it becomes interesting when we look at it quantum mechanically. We perform the SWAP test to achieve this, instead of delving into the details, all we need to know about the SWAP test is that it is non-deterministic. There is always a probability that it gives you the wrong answer.
What this means is that Bob can compare the values of ![]() that he found with
that he found with ![]() and, as we discussed earlier, the SWAP test can give incorrect results. Therefore, there will be a few mismatched bits (m). Now, as long as m is below a certain pre-fixed threshold Bob accepts the signature or else he rejects them as forgeries.
and, as we discussed earlier, the SWAP test can give incorrect results. Therefore, there will be a few mismatched bits (m). Now, as long as m is below a certain pre-fixed threshold Bob accepts the signature or else he rejects them as forgeries.
14. Conclusions
Quantum Cryptography is a beautiful combination of information theory and the laws of quantum mechanics. In our review we presented the basic laws of quantum mechanics, delved into a few Key distribution protocols, looked and how to counter eavesdroppers, real life attacks and finally at some non-key distribution protocols like data locking and digital signatures. The tremendous progress in quantum optics and optical fibers makes such protocols to be realized in the real world. Privacy Amplification (Sec X.), is a classical protocol heavily inspired from Quantum Cryptography. Though, Quantum Cryptography is mature there are still a lot of technological challenges that remain.
For example, the compatibility of the advanced detectors with the communication fibers. Another issue of Quantum Cryptography concerns its range, QC protocols even with modern range technology have a short distance range compared to other communication methods. Practical quantum repeaters could be the key for long range QC. Quantum repeaters detect and correct errors, provided error rate is low enough. We can hope that such techniques could potentially lead to realize QC over long distances. QC’s however still have many loopholes like side channel attacks, errors in random number generators and imperfection in the detectors which Eavesdropper’s can Exploit.
Despite these loopholes, humanity will master this technology and QC will become a commercial product potentially for secure financial transactions among other applications, we just do not know when that is going to happen.
About the author

Abhiram Cherukupalli
Abhiram is currently a junior in the Disha Delphi Public School. He is interested in quantum Ising models, superconductors, quantum information theory and developing nano-composites for super-capacitors.
