
Author: Suchismitaa Chakraverty
Vellore Institute of Technology, India
Abstract
How can we effectively use VPN to safeguard an IoT communication network? This study elucidates the procedure to set up a VPN tunnel over a home IoT network and analyzes its performance. In a world where every new day witnesses the addition of millions of new IoT nodes to the Internet, and innovative cyber-attacks are on the rise, ensuring the security of these networks is a burgeoning problem. To warrant assured communication over long distances, multiple VPN protocols have been developed over the years. A relatively new VPN protocol called WireGuard has been in use nowadays. This paper aims to analyze the network performance of WireGuard over an IoT network. Additionally, keeping in mind the resource-constrained nature of IoT environments, the research intends to provide a quantitative analysis of the energy consumption in the network through the measurement of CPU usage. In this manner, the study can be used to design energy-efficient IoT networks in the future.
Introduction
As technology is progressing and an increasing number of devices are getting connected to the Internet, the large-scale design and deployment of IoT networks have been on the rise. A substantially good method therefore to ensure secure communication is the introduction of a VPN to isolate and mask critical communications. A comparatively recent protocol, the motivation behind using WireGuard for this study is its considerably simpler administration method. Surpassing the complexities of IPSec, WireGuard provides ‘wg0’ as the virtual interface which can be configured with a private key and the public keys of its communicating peers. Most of the crucial functions like connection setup, connection teardown, exchange of keys, etc. are hidden from the operator. The justifiability of WireGuard lies in the fact that it has a small codebase of merely 4000 lines. Compared to OpenVPN which operates in the user space and delivers quite a poor performance[1], WireGuard’s network throughput is almost comparable to the network delivery when it is operating without a VPN, as has been shown in the study.
The study conducted has leveraged Iperf tool- a popular network performance measurement tool for generation of network traffic[2]. The Iperf tool operates on a client-server model. Network traffic throughput has been measured in both directions by reversing the roles of Iperf client and server on the component devices. This has been done to ensure that choosing an Iperf client or server can be arbitrary and it poses no dependency to the experiment whatsoever. 2 4 gB RAM Raspberry Pi operating systems have been used to deploy the WireGuard server and client respectively. Despite their significant perks, VPNs do suffer a disadvantage owing to their resource-intensive nature.IoT networks are resource-constrained environments and not likely to support high energy operations[3]. Therefore, keeping this thought in mind, the study has provided a comprehensive measurement of CPU usage with VPN switched on and without VPN.
As a direct consequence, this research can be anchored for the wide scale development of future energy efficient IoT networks.
Related Work
Over the years, numerous security technologies have been invented to protect against newer threats and vulnerabilities emerging everyday. With the design and launch of VPNs, extensive studies have been conducted to verify their security and performance credibilities. Some of the earliest works include analyzing the security that VPNs provide over normal communication channels and how the feature can be enhanced furthermore through standardization of governing protocols. Predominantly, the popular VPN protocols like IPSec, OpenVPN and GRE have been compared with WireGuard[4].
With the emergence of different operating systems to meet specific user needs, security of these budding software packages have raised an important concern. As a result, in-depth research has been conducted to measure VPN performance when operated in vastly contrasting environments like Linux, Windows, ROS to name a few. The results have proved consequent results of measured network performance to be disparate owing to the differing design nature of the underlying kernel of these OS.
To facilitate a broad range of business outcomes, specific VPNs have been designed. The most common ones among these are Remote Access VPN, Site to Site VPN, Intranet based VPN and Extranet based VPN. Remote Access VPN caters to the scenario when a geographically distant user happens to get attached to a closed network. The connection is safe and is set up within the Internet. Site to Site VPN is leveraged when connection channels are required from one office location to the network at additional office locations, i.e. typically between headquarters and branch offices. Intranet based VPN enables offices of similar companies to remain tied to a single protected network with the usage of Site to Site VPN. Likewise Extranet based VPN is deployed to facilitate connection between dissimilar company networks.
On account of the increasing advances in the containerization domain in recent years, WireGuard performance has been systematically analyzed formerly in a Kubernetes cluster[5]. The results displayed that component nodes of the cluster when tunneled using WireGuard had greater response time indicating poorer performance as compared to the condition of operation of the cluster in an environment without WireGuard. Therefore, keeping an analogy with the previously mentioned study, this research aims to compare network performances in an Ethernet LAN network operating with and without WireGuard. Additionally, the CPU usage has been quantized for both the scenarios providing an insight into the network’s energy efficiency in different conditions.
Methodology & Experimental Setup
To measure the network performance and CPU usage of the component nodes, the methodology that was adopted to setup the lab is described below:-
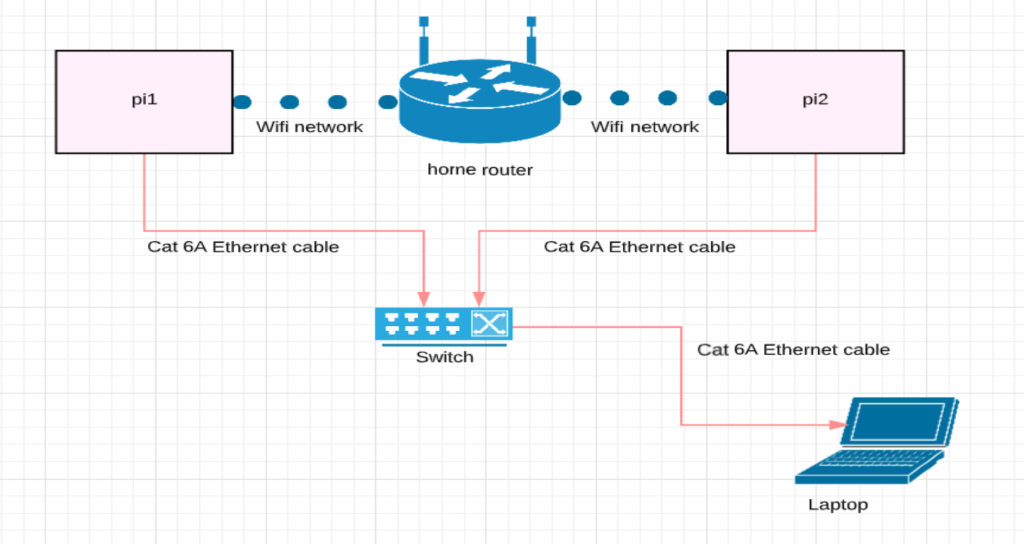
- 2 standard Raspberry pi 4 model B with 4 gB RAM(specifications given in Appendix) installed with Raspbian OS served as the prime components of the network
- Cat 6A Ethernet cables were used to connect the Raspberry pi’s to the home router. This was primarily done to achieve SSH connection on both the SOC’s.
- A Windows 10 laptop was used in order to remotely control the Raspberry pi devices.
- For measuring network performance, popular network bandwidth testing tool, Iperf was leveraged for generating network traffic. Dstat tool was leveraged for measuring CPU usage[6]. The generated traffic stream was maintained at 1gb/s for both the experiments and measurements were recorded within a time interval of about 10 s.
- Iperf operates on a client-server model. To ensure the ubiquity of the experiment, the client and server roles were periodically reversed amongst the Raspberry pi devices.
- To measure the CPU usage of the component devices, again the Iperf tool was deployed for generating traffic. The resulting CPU usage was recorded with the Dstat tool. Total CPU usage was computed by taking the summation of user CPU usage and system(kernel) CPU usage. As done previously, the IPerf client and server roles were reversed amongst the component pi devices to ensure the ubiquity of the experiment.
- Both network performance and CPU usage measurements have been taken in environments with and without WireGuard VPN to explicitly determine the positive and negative implications of introducing VPN to a network.
Results & Discussion
The graphical results obtained have been illustrated as follows:-
Network Performance Measurement
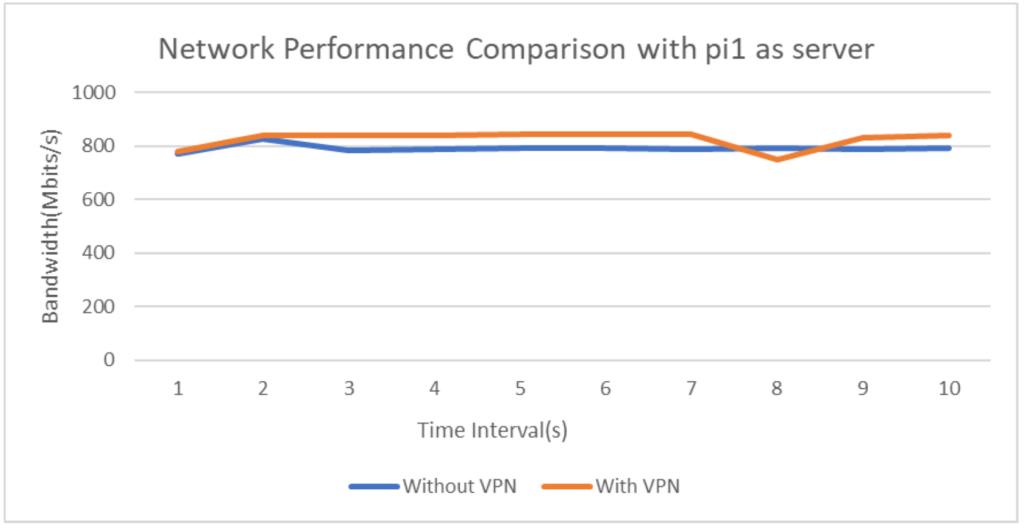
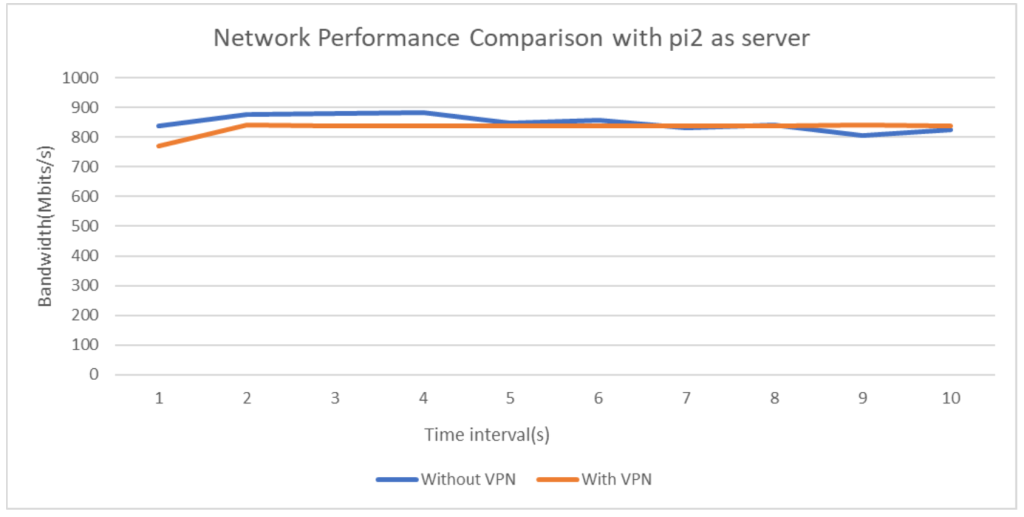
To compare and analyze network performance in scenarios with and without VPN, the network throughput has been recorded and plotted for a time interval of 10s(Fig 2 and 3). Since the Iperf tool works on a client server model, to assure the ubiquity of the experiment both the raspberry pi devices, pi1 and pi2 have been assigned the server and client roles alternatively for the readings.
CPU usage measurement
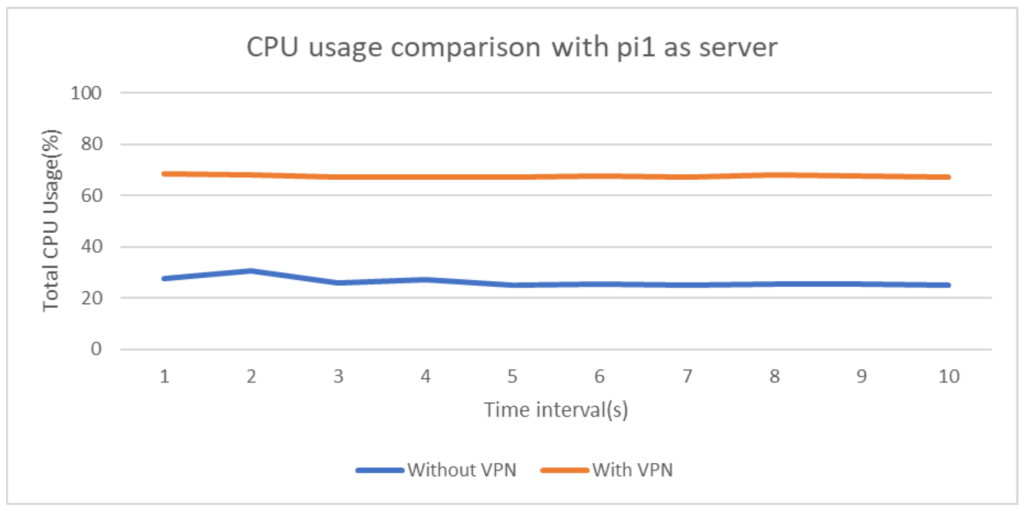
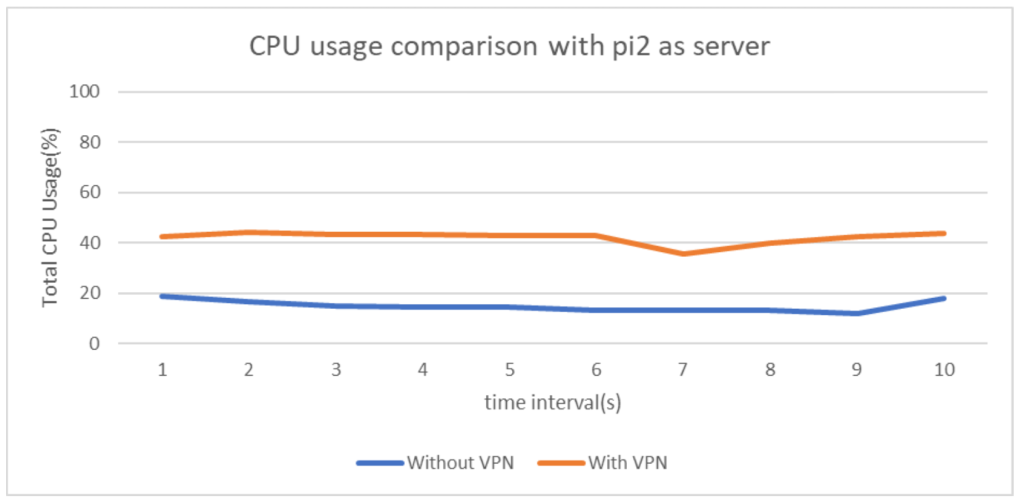
For measuring and analyzing CPU usage in conditions of operation with and without VPN, total CPU usage which is the summation of user process CPU usage and system process CPU usage has been recorded and plotted for a time interval of 10s(Fig 4 and Fig 5). Both Raspberry pi devices, pi1 and pi2 again have been assigned Iperf client and server roles alternatively to ensure the credibility of the results obtained.
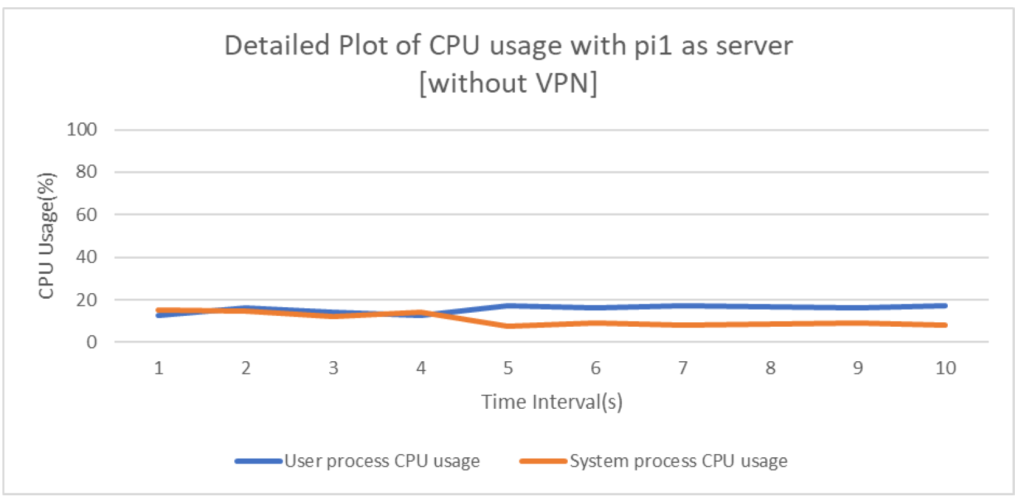
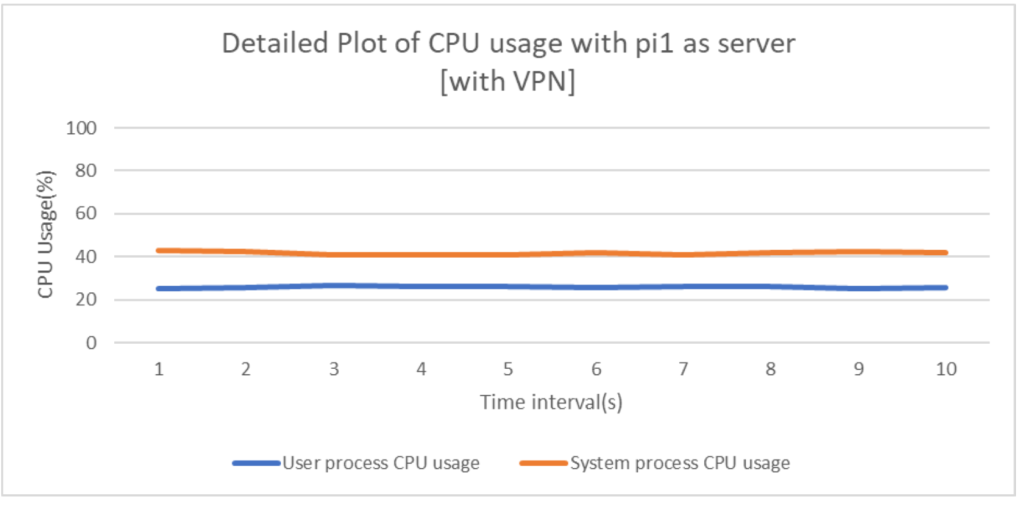
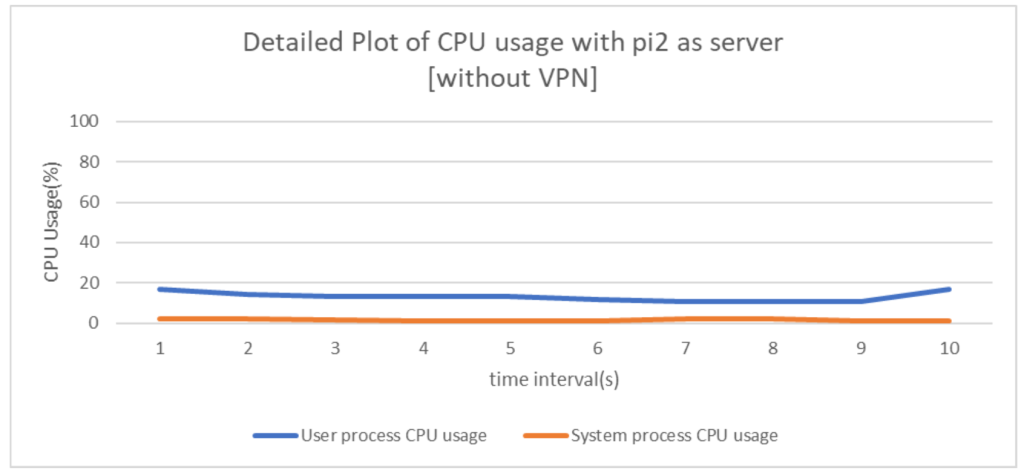
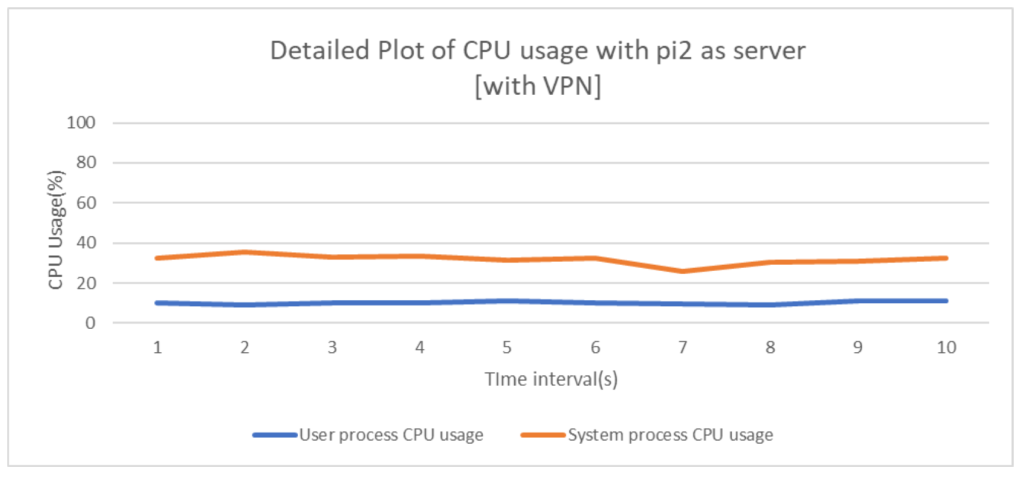
The above graphs(Fig 6, Fig 7, Fig 8 and Fig 9) depict the individual components i.e. user process CPU usage and system process CPU usage in both operation scenarios of with and without VPN by assigning both the devices, pi1 and pi2 as Iperf server and client alternatively.
From the above plots it is evident that usage of WireGuard gives comparable network performance(even better in some cases) when measured w.r.t normal Ethernet LAN networks. This is indeed a great positive aspect of the protocol as it ensures that network communications are in no way undermined even if WireGuard is added which provides the much needed security against disastrous attacks. Analyzing the CPU usage in both the scenarios, it can be concluded that addition of VPN considerably increases the number of CPU cycles thus rendering the network as a high energy consuming one, which is an important downside of VPN installed networks.
Conclusion and Future Work
Throughout this study, emphasis has been laid on analyzing the perks and pitfalls of VPN(Wireguard) networks when compared with normal Ethernet networks. It has been noted that, as contrasted with its peers, WireGuard provides comparable network performance keeping pace with the throughput of Ethernet networks. From the aspect of energy efficiency, VPN networks are less energy efficient or more resource costly networks. This is because of the added CPU cycles with the addition of VPN tunneling. All the experiments have been conducted by maintaining a network stream of 1 gB/s within a time interval of 10 s. As a next step, further studies can be conducted by altering the network stream or increasing the time interval. Conclusively, as the deployment of secure networks is gaining widespread importance over the years, this research can be instrumental in the future development of energy efficient secure communication networks with considerably good performance.
References
[1]Jason A. Donenfeld, “WireGuard: Next Generation Kernel Network Tunnel”, NDSS, 2017 [2]Fatih Abut and Martin Leischner, “An Experimental Evaluation of Tools for Estimating Bandwidth-Related Metrics”, International Journal of Computer Network and Information Security, 2018
[3]Bassel Al Homssi, Akram Al-Hourani, Sathyanarayanan Chandrasekharan, Karina Mabell Gomez and Sithamparanathan Kandeepan, “On the Bound of Energy Consumption in Cellular IoT Networks”, IEEE Transactions on Green Communications and Networking, Vol 4, Issue 2, pg 355-364, June 2020
[4]Adnan Mohsin Abdulazeez and Baraa Wasfi Salim, Diyar Qader Zeebaree and Dana Doghramachi, “Comparison of VPN protocols at Network Layer Focusing on Wire Guard Protocol”, learntechlib.org, 2020
[5]Pavan Gunda and Sri Datta Voleti, “Performance evaluation of wireguard in kubernetes cluster”, Faculty of Computing, Blekinge Institute of Technology, 2020
[6]Tribid Debbarma and K Chandrasekaran, “Comparison of FOSS based Profiling Tools in Linux Operating System Environment”, 2nd International Conference on Contemporary Computing and Informatics, 2016
[7]Kotuliak, P. Rybár and P. Trúchly, “Performance comparison of IPsec and TLS based VPN technologies”, 9th IECTA(International Conference on Emerging eLearning Technologies and Applications), 2011
[8]T. Berger, “Analysis of current VPN technologies”, First International Conference on Availability, Reliability and Security, 2006
[9]Shaneel Narayan, Kris Brooking and Simon de Vere. “Network Performance Analysis of VPN Protocols:An Empirical Comparison on Different Operating Systems”, International Conference on Networks Security, Wireless Communications and Trusted Computing, 2009
[10]Maximilian Pudelko, Paul Emmerich, Sebastian Gallenmüller and Georg Carle, “Performance Analysis of VPN Gateways”, IFIP Networking Conference, 2020
[11]Zheng Wu and Mingzhong Xiao, “Performance Evaluation of VPN with Different Network Topologies”, IEEE 2nd International Conference on Electronics Technology, 2019
[12]S. Padhiar, & Verma, P., “A Survey on Performance Evaluation of VPN”, International Journal of Engineering Development and Research, vol. 3, no. 4, pp. 516-519, 2015.
[13]K. Rao, Rao, N., Sitharam, M., Vardhan, K. A., & Routhu, P. K., “A Study on Performance Analysis of IPSec VPN and MPLS VPN”, International Journal of Futuristic Science and Technology, vol. 1, no. 3, pp. 184-190, 2013.
[14]R. Prosad et al., “Bandwidth estimation: metrics, measurement techniques, and tools”, IEEE Netw., vol. 17, no. 6, pp. 27–35, 2003.
[15]A. S. Sairam, “Survey of Bandwidth Estimation Techniques”, Wirel. Pers. Commun., pp. 1425–1476, 2015.
[16]A. Tirumala, L. Cottrell, and T. Dunigan, “Measuring end-to-end bandwidth with Iperf using Web100”, Proc. Passiv. Act. Meas. Work., pp. 1–8, 2003.
[17]F. Abut, “Towards a Generic Classification and Evaluation Scheme for Bandwidth Measurement Tools”, Signals Telecommun. J., vol. 1, no. 2, pp. 78–88, 2012.
[18]A. J. Patel, & Gandhi, A., “A survey on performance evaluation of VPN”, International Journal of Advance Engineering and Research Development, vol. 4, no. 3, pp. 516-520, 2017. [19]J. A. Donenfeld, & Milner, K., “Formal verification of the wire guard protocol”, 2017.
[20]P. Wu., “Master’s Thesis: Analysis of the Wire Guard protocol”, Department of Mathematics and Computer Science, Eindhoven University of Technology 2019.
Appendix
Specifications of Raspberry pi device used in the experiment:-
- 2.4 GHz and 5.0 GHz IEEE 802.11ac wireless, Bluetooth 5.0, BLE Gigabit Ethernet
- 2 USB 3.0 ports, 2 USB 2.0 ports
- Raspberry Pi standard 40-pin GPIO header (fully backward compatible with previous boards)
- 2 × micro-HDMI ports (up to 4kp60 supported),
- 2-lane MIPI DSI display port
- 2-lane MIPI CSI camera port
- 4-pole stereo audio and composite video port
- H.265 (4kp60 decode), H264 (1080p60 decode, 1080p30 encode)
- OpenGL ES 3.1, Vulkan 1.0
- Micro-SD card slot for loading operating system and data storage
- 5V DC via USB-C connector (minimum 3A*)
- 5V DC via GPIO header (minimum 3A*)
- Power over Ethernet (PoE) enabled (requires separate PoE HAT)
- Operating temperature: 0 – 50 degrees C ambient
About the author

Suchismitaa Chakraverty
Suchismitaa is a Computer Science and Engineering major who graduated from Vellore Institute of Technology, India. Her interests lie in computer networking and security. Currently, she is a consulting engineer at Cisco where she troubleshoots customer network problems on a daily basis. Her extracurricular interests include public speaking (debating and extempore), traveling, and writing.
